Safety vs. Security: Understanding the Differences and How They Integrate in Embedded Software
15 Jul, 2025By the end of 2025, over 55.9 billion devices will be connected worldwide. This explosion of connectivity places critical systems alongside the mundane and dispensable. The infamous tale of a casino’s database being scraped through a thermometer in its lobby fish tank is a stark reminder that while a device may seem secure in isolation, that isolation no longer exists. In industries where failures are not just costly but potentially catastrophic, such as automotive, aerospace, and medical devices, ensuring that systems are both safe and secure is no longer optional. Understanding these differences is vital for designing robust systems that protect against both accidental failures and malicious attacks, but how do you strike the right balance between these two critical elements? This blog will explore the differences and integration of cybersecurity and functional safety in embedded systems.
What Is Cybersecurity in Embedded Software?
Embedded security protects a device’s internal components, including hardware, operating system, applications, and data, using features such as encryption and secure boot mechanisms. It encompasses security throughout the entire lifecycle of the device, starting from the design phase, protecting the device from potential threats, and continuing through to its decommissioning.
Whereas, cybersecurity is a key component of embedded systems security and focuses on defending the device from network-based attacks, protecting it from hacking, data breaches, and other external threats. ISO 27032 defines cybersecurity as the “preservation of confidentiality, integrity and availability of information in the Cyberspace” and “Cyberspace” as “the complex environment resulting from the interaction of people, software and services on the Internet by means of technology devices and networks connected to it, which does not exist in any physical form”. Both embedded security and cybersecurity are crucial for safeguarding embedded systems.
Cybersecurity with ISO 21434
Cybersecurity plays a critical role in the ISO 21434 standard, which focuses on managing cybersecurity risks in road vehicles throughout their lifecycle. It outlines road vehicle cyber security as a “road vehicle cybersecurity condition in which assets are sufficiently protected against threat scenarios to items of road vehicles, their functions and their electrical or electronic components.” ISO 21434 outlines the necessary processes for identifying, assessing, and mitigating security threats that could impact automotive systems. It emphasizes the importance of integrating cybersecurity into every phase of vehicle development, from initial design to post-production support and for every component – from the safety-critical systems to the comfort features such as wireless climate control and infotainment. By ensuring that appropriate security measures are implemented, including secure software development practices, risk assessments and ongoing monitoring, ISO 21434 helps manufacturers safeguard vehicles against evolving threats. The standard fosters a holistic approach to cybersecurity, where both the vehicle’s components and the broader supply chain must work together to ensure robust protection.
Out of Context Application and TARA (Threat Analysis and Risk Assessment)
One of the challenges in developing secure embedded systems for road vehicles is performing a thorough Threat Analysis and Risk Assessment (TARA). This process involves evaluating potential security risks and threats based on the context in which the system will be deployed.
When a system is considered out of context, meaning that it has been developed for general-purpose use rather than for a specific application, making accurate security assessments can be difficult. Without knowing how the system will be used, it’s challenging to identify the threats that are most relevant to the device.
When the deployment context is unknown, no assumptions can be made about the operating environment and therefore all security analysis must be based on the worst-case scenarios, which may include considering open access or that certain security features, such as encryption or secure boot, may be missing. If the environment for the embedded system is known in advance, more accurate assumptions can be made about the system’s security requirements and capabilities. Knowing factors like network architecture, data flow, and external interactions can allow developers to tailor the security features of the embedded system.
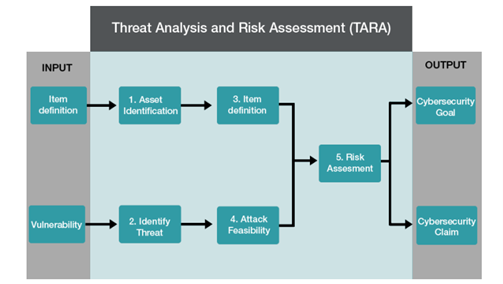
Figure 1 Summary of the TARA Process
How Cybersecurity Integrates with Functional Safety
Functional safety refers to ensuring that embedded systems continue to operate as intended, even in the event of a failure or fault. The goal is to minimize the risk of harm to people, equipment, or the environment by ensuring that safety-critical systems can detect and respond to faults appropriately.
While cybersecurity and functional safety address different challenges, they are increasingly becoming interdependent, especially in the context of modern, connected embedded systems. Both aim to protect the system from failure, security focuses on external threats, while functional safety focuses on internal system failures.
To integrate cybersecurity with functional safety, systems must be designed with both in mind from the outset. For example, a safety-critical application such as a car, not only needs to ensure that it functions correctly under normal circumstances but also needs to defend against cyberattacks that could compromise its operation. A breach could lead to dangerous situations such as malfunctioning brakes or airbags. By applying standards such as ISO 26262 for functional safety and ISO 21434 for cybersecurity, developers can ensure that both aspects are adequately addressed throughout the development lifecycle.
Moreover, cybersecurity can enhance functional safety by preventing attacks that could disrupt the device’s safe operation. For example, an attacker who gains control over a safety-critical system could trigger harmful failures. Thus, protecting the system from cybersecurity threats directly supports its overall safety and reliability.
Consider Using a Safety-Critical RTOS
When developing safety-critical systems, it’s important to choose an RTOS that supports both functional safety and cybersecurity. A safety-critical RTOS is designed to meet stringent reliability and safety standards while also incorporating security features to defend against cyberattacks. For example, SAFERTOS® is pre-certified to IEC 61508 and ISO 26262 and is developed in accordance with ISO 21434. SAFERTOS® provides features such as memory protection, fault tolerance, and real-time monitoring that ensure systems can both withstand failures and defend against cyberattacks. Furthermore, it incorporates an Enhanced Security Module (ESM), which adds an extra layer of defence against potential cyberattacks, safeguarding your system’s integrity. By choosing SAFERTOS®, developers not only enhance system resilience but also simplify the certification process, reducing costs and time-to-market.
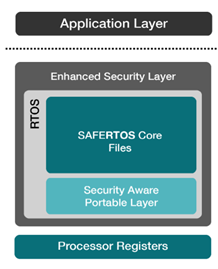
Figure 2 SAFERTOS® and the ESM
Summary
In the embedded systems world, safety and security go hand in hand. While safety ensures that the system will behave correctly and avoid harming users or the environment, security ensures that the system can resist malicious attacks that might undermine its safety. By understanding the differences between safety and security and integrating them effectively, developers can build more resilient, secure, and reliable embedded systems. Whether designing for a known application or working with out-of-context components, performing a thorough TARA and making informed assumptions about the environment is essential to protecting the system from threats. As embedded systems evolve to become more interconnected, integrating cybersecurity with functional safety will be critical to ensuring their safe and secure operation in an increasingly complex world.
Are you ready to build safe and secure embedded systems? Contact us to learn how our expertise can help you integrate safety and security seamlessly.
Author
Jonny Slim, Senior Software Engineer

